SSO with Azure AD via OpenID Connect
Updated
To get started with using SSO to login to Kundo with your Azure account, contact us at support@kundo.se with the settings generated in this guide.
In summary, you will send us three values on Kundo:
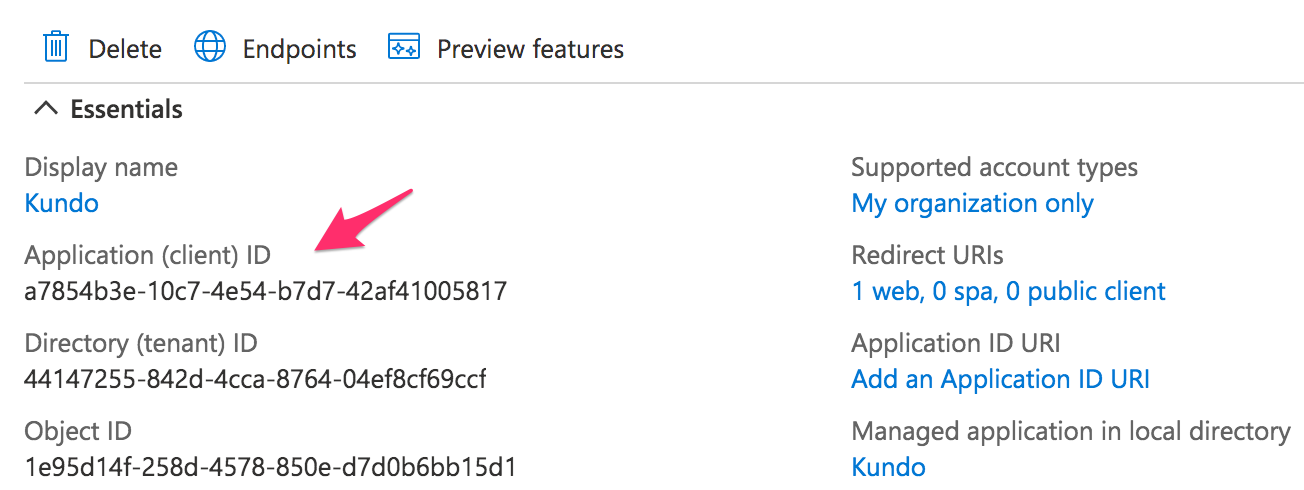
- The Client ID value from the Overview page
- The Client Secret value from the Certificates & Secrets menu
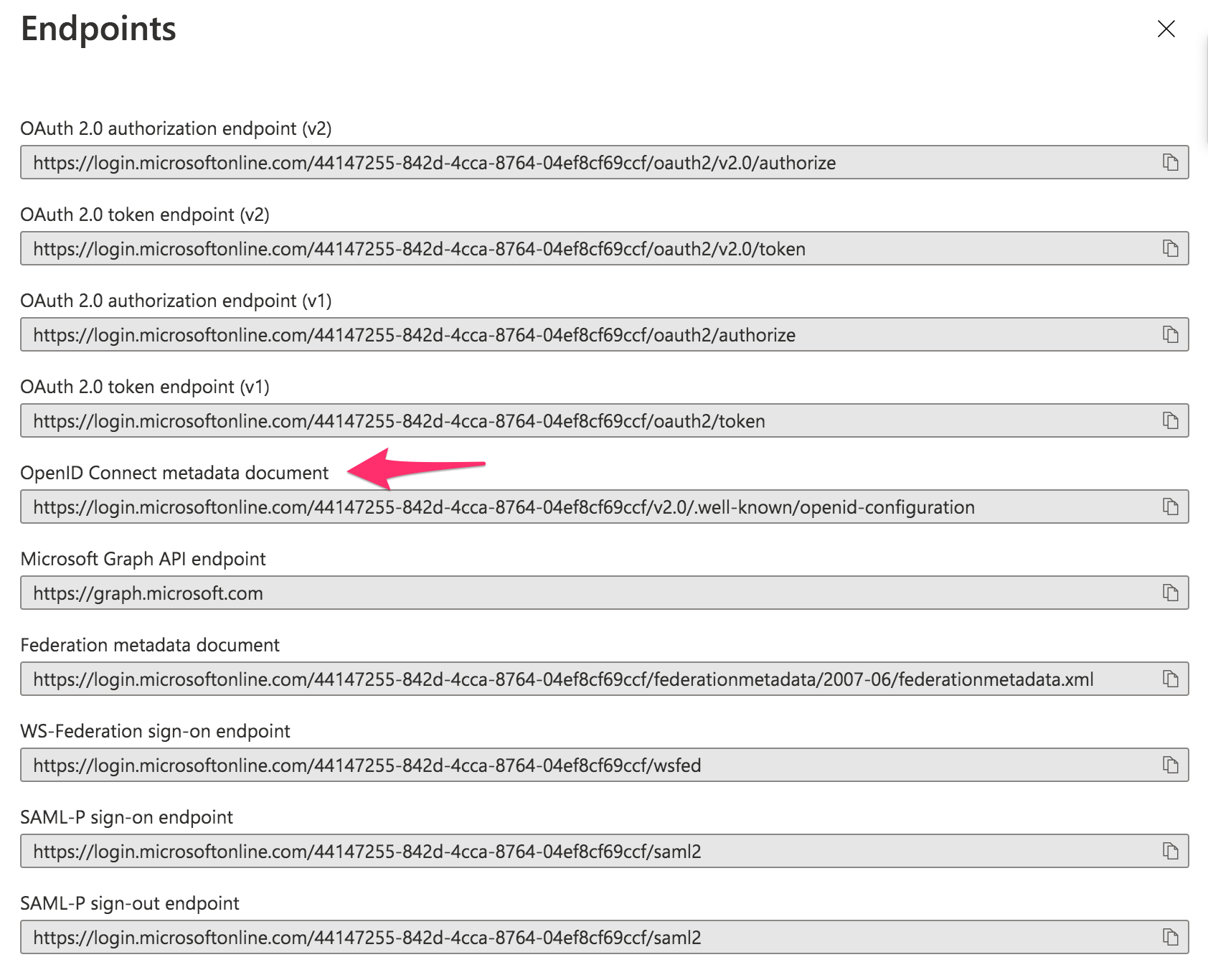
- The URL found in Endpoints > OpenID Connect Metadata document
If possible, you are also welcome to send the information for a test user, so we have the opportunity to help you test the configuration before it is activated for your users.
Step-by-step instructions
- Go to the Active Directory page in your Azure portal.
- Go to App Registrations > New Registration.
- Fill in Name: "Kundo" and Redirect URI of type "Web" with the value "https://auth.kundo.se/oauth2/callback/" and then click on "Register".
- You will now come to an overview page for the app registration. Copy the Application (client) ID and Endpoints > OpenID Connect Metadata document values.
- Go to Certificates & Secrets > New client secret.
Add a "client secret" and copy the value for later. - Go to Token Configuration > Add optional claim and add "email" and "upn" under the token type "ID".
- Go to Branding and add a Kundo logo and title to the App registration.
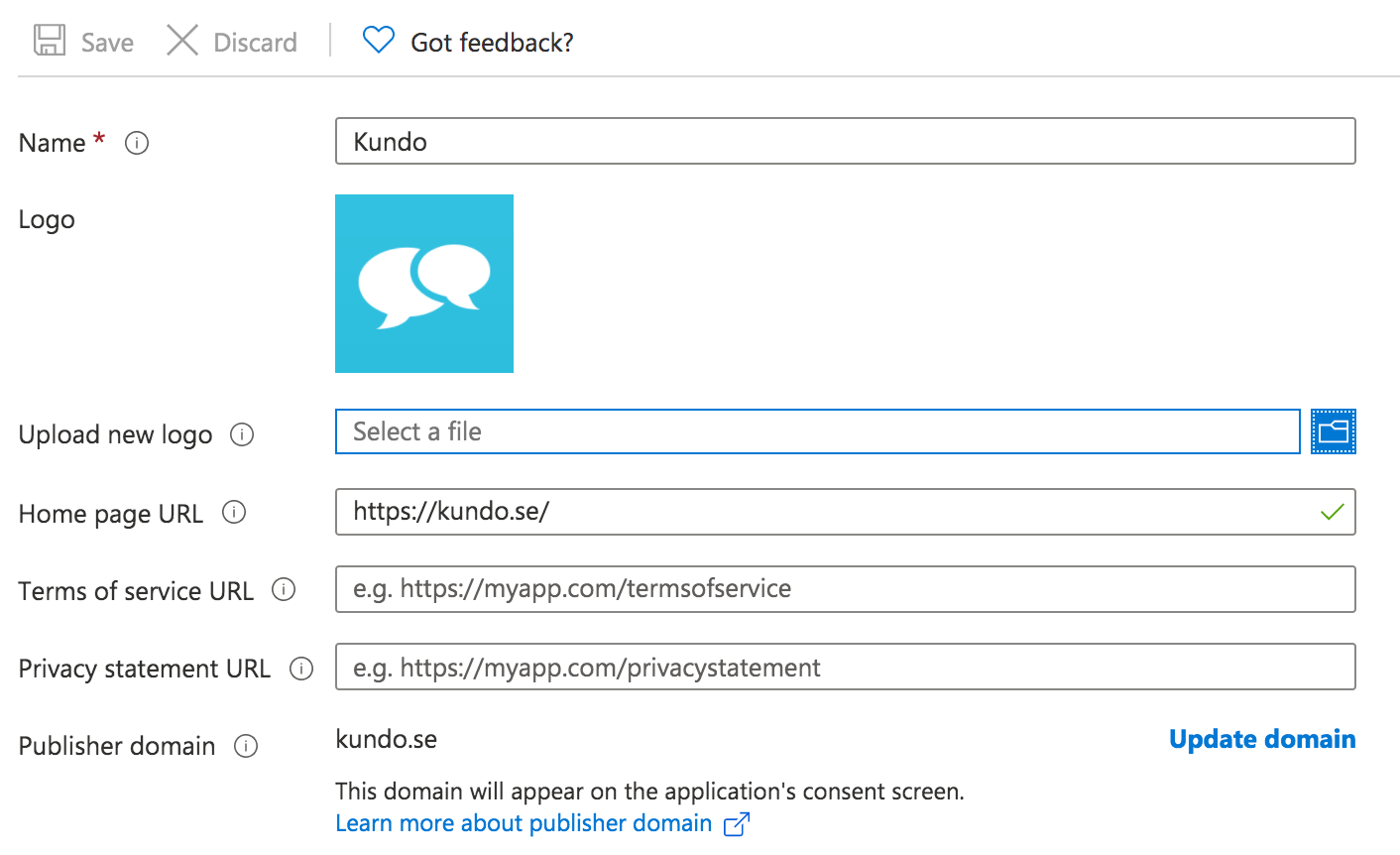
You are welcome to use this logo:
- Do not forget to give access to the app for your users.
- Done!
Send the values you've copied to us at support@kundo.se and we will complete the configuration and get back to you.